Draft:Cybersecurity
Cybersecurity awareness[edit]
Cybersecurity is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. It aims to protect individuals and organizations’ systems, applications, computing devices, sensitive data, and financial assets against simple and annoying computer viruses, sophisticated and costly ransomware attacks, and everything in between. Cybersecurity specialists should have at least a bachelor’s degree in computer science or a related subject, and experience working in cybersecurity, such as an internship or apprenticeship, is important. Expert-level IT skills are a must, including knowledge of advanced analytics, artificial intelligence, and automation to fight cyber threats more effectively and minimize the impact of cyberattacks when they occur.
| Submission declined on 13 October 2023 by Phuzion (talk). Thank you for your submission, but the subject of this article already exists in Wikipedia. You can find it and improve it at Computer security instead.
Where to get help
How to improve a draft
You can also browse Wikipedia:Featured articles and Wikipedia:Good articles to find examples of Wikipedia's best writing on topics similar to your proposed article. Improving your odds of a speedy review To improve your odds of a faster review, tag your draft with relevant WikiProject tags using the button below. This will let reviewers know a new draft has been submitted in their area of interest. For instance, if you wrote about a female astronomer, you would want to add the Biography, Astronomy, and Women scientists tags. Editor resources
|  |
| Submission declined on 5 April 2023 by Blaze Wolf (talk). Thank you for your submission, but the subject of this article already exists in Wikipedia. You can find it and improve it at Computer security instead. Declined by Blaze Wolf 13 months ago. |  |
Cybersecurity refers to the protection of computer systems, networks, and data including the infrastructure, processes, physical systems, and people depending on those computer systems, from theft, damage, or unauthorized access. It involves the use of technology, processes, and practices to safeguard digital information from threats such as cybercrime, espionage, and hacktivism. According to NIST cybersecurity is "The ability to protect or defend the use of cyberspace from cyber attacks.".[1] Cybersecurity should be differentiated from other types of computer security and information security, covering not only the protection of information or computers, but also protecting the infrastructure, services and supply chains dependent on information technology and communication systems. This includes the concept of a Cyber-physical_system and other processes which are not technology but depend on technology. CISA defines cybersecurity as the "art of protecting networks, devices, and data from unauthorized access or criminal use and the practice of ensuring confidentiality, integrity, and availability of information."[2]
Cybersecurity is also defined by NIST as "Prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation."[1]
Cybersecurity is becoming increasingly important as technology continues to advance and more information and activities are used, processed, stored and carried-on in the cyberspace and with online services. It is essential for protecting sensitive data such as personal information, financial records, and intellectual property, not only for data or information management, but to support, automate and efficient work and activities of all kinds, applied to all productive, entertainment and personal sectors leading to an exponential growth in the number of connected devices, activities and services. For example, we find connected devices for the control and automation of home functions - called home automation or domotics - such as on and off lights, climate control and air conditioning, opening and closing doors, among others. In the same way in the business environment, we find devices that control alarms, elevators, fire monitoring and control, room automation, access control of staff and visitors, and many other applications for industrial control system. Connected cars, medical devices – including some inserted into the human body, such as pacemakers and insulin pumps – are increasingly coming to market, along with the connection of power, gas and other commodities.
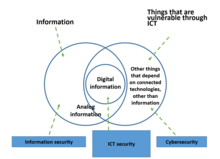
Therefore, cybersecurity is related to information security and computer security, but also considers the protection of related infrastructure, products and services. Then cybersecurity is the protection of information and telecommunication technologies (ICT), the data processed and the infrastructure, products and services depending on them.[3]
According with Information Systems Audit and Control Association (ISACA) cybersecurity is "the protection of information assets by addressing threats to information processed, stored, and transported by internet worked information systems"[4] according to which there are several key components of cybersecurity, including:
- Network security: This involves protecting the network infrastructure from unauthorized access, attacks, and other security threats.
- Endpoint security: This refers to securing individual devices such as laptops, smartphones, and tablets from malware, viruses, and other cyber threats.
- Application security: This involves securing applications and software programs from attacks and vulnerabilities.
- Data security: This involves protecting sensitive data from theft or unauthorized access through encryption, access controls, and other measures.
- Identity and access management: This involves ensuring that only authorized users have access to sensitive data and systems, and that their identities are properly authenticated.
Cybersecurity professionals use a range of tools and techniques to protect systems and data from cyber threats. These include firewalls, intrusion detection and prevention systems, antivirus software, encryption, and vulnerability scanners.
History[edit]
Cybersecurity has its origins in the early days of computing. As computers became more integrated into business and government functions, the need to protect sensitive information became evident, so the history of cybersecurity starts in computer security. This history is marked by a continuous conflict between attackers and defenders, with significant incidents and breakthroughs including:
1970s-1980s: Emergence of the first computer viruses and the realization of the need for computer security. 1990s: Rise of the Internet and the proliferation of cybercrimes. 2000s: Notable cyberattacks on major corporations and government entities. 2010s: Increased awareness and investment in cybersecurity, with a focus on cyber warfare and critical infrastructure protection.
Cybersecurity started to become a concern not just for computer users but to the general public, and this became evident with attacks like the 2007 cyberattacks on Estonia which caused impact not just to the computer systems, but to the physical infrastructure providing power to a city in Estonia. Another example of these impacts beyond the computer realm was the Colonial Pipeline ransomware attack in 2021, which caused the halt of the pipeline operations for more than 5 days [5]
International[edit]

The International Telecommunication Union publishes the Global Cybersecurity Index[6] and measures five pillars for cybersecurity in the surveyed countries:
- legal measures;
- technical measures;
- organizational measures;
- capacity development measures;
- cooperation measures.
This makes clear that in addition to technical measures, cybersecurity also involves educating users about safe online behavior and implementing policies and procedures to ensure that data is handled securely, and presenting it as an ongoing process that requires constant vigilance and adaptation to evolving threats.
References[edit]
- ^ a b "NIST Cybersecurity". NIST Glossary. NIST.
- ^ "CISA Cybersecurity". CISA security tips. CISA. February 2021.
- ^ Corona Fraga, Pablo (July 2019). Practical Guide for risk management in the age of cybersecurity. Mexico. p. 39. ISBN 978-607-474-479-8.
{{cite book}}: CS1 maint: location missing publisher (link) - ^ "ISACA Glossary" (PDF). ISACA Glossary. Retrieved 29 January 2022.
- ^ Lyons, Kim (May 15, 2021). "Colonial Pipeline says operations back to normal following ransomware attack". The Verge.
- ^ "Global Cybersecurity Index". ITU-T Global Cybersecurity Index. ITU-T.
